The HITCON 2017 CTF “Data & Mining” challenge:
The file attached was a 230MB big pcapng file.
I think I solved this by accident. I was sifting through the data for a bit and started to exclude the flows with a huge amount of data as it was mostly compressed / unreadable to me.
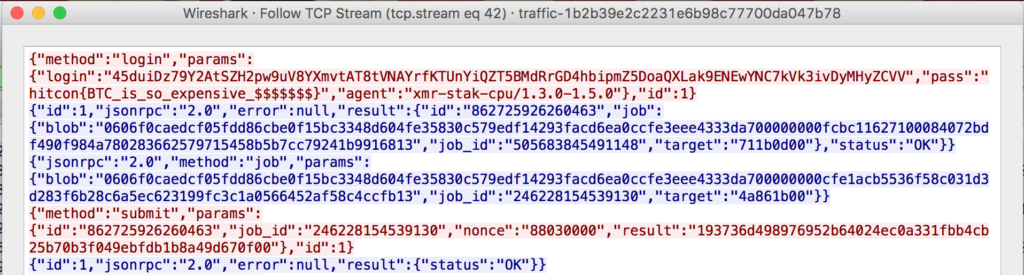
In the remaining data I stumbled over a plaintext TCP stream on port 3333:
This contained the flag in plaintext: hitcon{BTC_is_so_expensive_$$$$$$$}
In retrospective, searching for the string hitcon in the packet data would have worked as well.

grep *.pcapng | grep hitcoin

I didn’t solve this challenge because of the speed of my internet… The file was very big