The NeverLAN CTF challenge JSON parsing 1:
The linked file can be found here.
The JSON file contains a minute of VirusTotal scan logs. The challenge wants us to find the 5 AV engines which had the highest detection ratio (not detection count) in that timeframe. To solve it I created this quick Python script:
from __future__ import division
import json
result_true = {}
result_false = {}
result_ratio = {}
with open('file-20171020T1500') as f:
for line in f:
data = json.loads(line)
for scanner in data['scans']:
if data['scans'][scanner]['detected'] == True:
if scanner in result_true:
result_true[scanner] += 1
else:
result_true[scanner] = 1
else:
if scanner in result_false:
result_false[scanner] += 1
else:
result_false[scanner] = 1
for scanner in result_false:
result_ratio[scanner] = result_true[scanner] / (result_true[scanner] + result_false[scanner]) * 100
for key, value in sorted(result_ratio.iteritems(), key=lambda (k,v): (v,k)):
print "%s: %s" % (key, value)
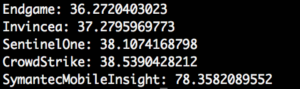
It will count detection for each AV engine and afterwards calculate the detection ratio for all. Running it will print all ratios sorted by lowest to highest. The last 5 separated by commas is the flag:
The flag is: SymantecMobileInsight,CrowdStrike,SentinelOne,Invincea,Endgame