Following up a bit on my recent post “Looking at public Puppet servers” I was wondering how an attacker could extend his rights within the Puppet ecosystem especially when a system like Foreman is used. Cross site scripting could be useful for this, gaining access to Foreman would allow an attacker basically to compromise everything.
I’ve focused first on facts. Facts are generated by the local system and can be overwritten given enough permissions. Displaying facts in the table seemed to be secured sufficiently, however there is another function on the /fact_values page: Showing an distribution graph of a specific fact.
When the graph is displayed HTML tags are not removed from facts and XSS is possible. Both in the fact name (as a header in the chart) and fact value (in the legend of the chart).
For example, add two new facts by running:
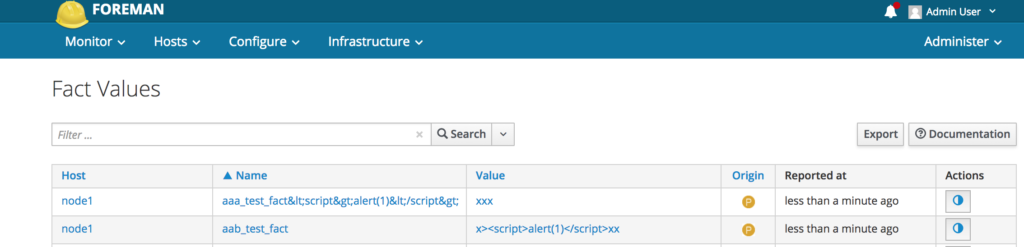
mkdir -p /etc/facter/facts.d/ cat << EOF >> /etc/facter/facts.d/xss.yaml --- aaa_test_fact<script>alert(1)</script>: xxx aab_test_fact: x<script>alert(1)</script>xx EOF
It will shop up like this in the global /fact_values page:
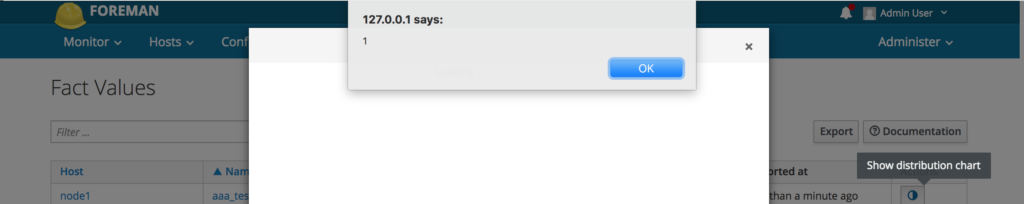
Clicking on the “Show distribution chart” action on either of those facts will execute the provided alert(1) JavaScript:
That’s fun but not really useful, tricking someone to click on the distribution chart of such a weird fact seems impractical.
But since the XSS is in the value of the fact we can just overwrite more interesting facts on that node and hope that an Administrator wants to see the distribution of that fact. For example, let’s add this to xss.yaml:
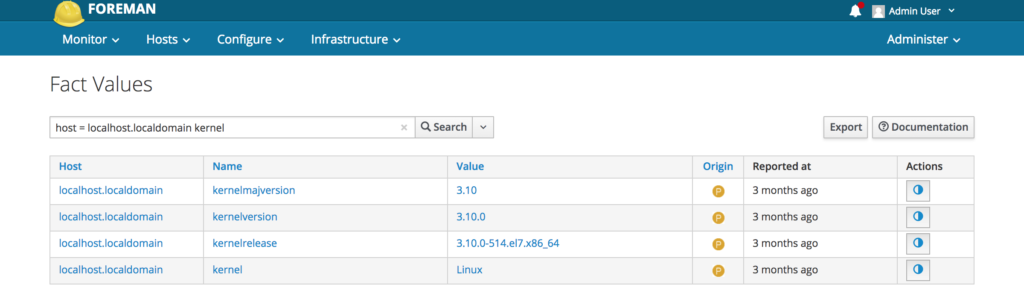
kernelversion: x><script>alert(1)</script>xx
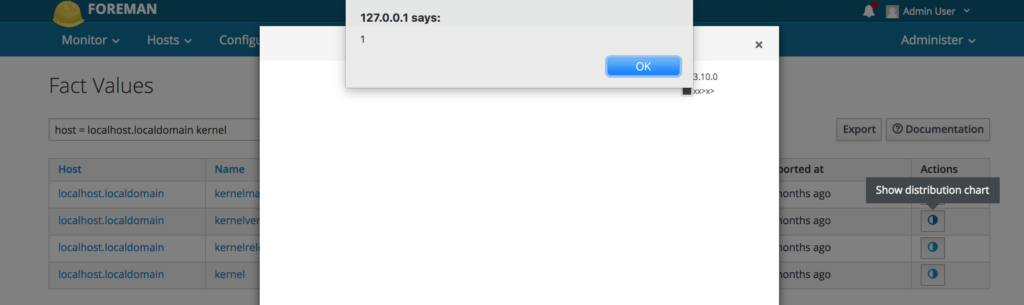
Now if an Administrator wants to know the distribution of kernel versions in his environment and he uses this chart feature on any host the alert(1) JavaScript will get executed. This is what any other node will look like:
And after navigating to the kernelversion distribution chart on that page:
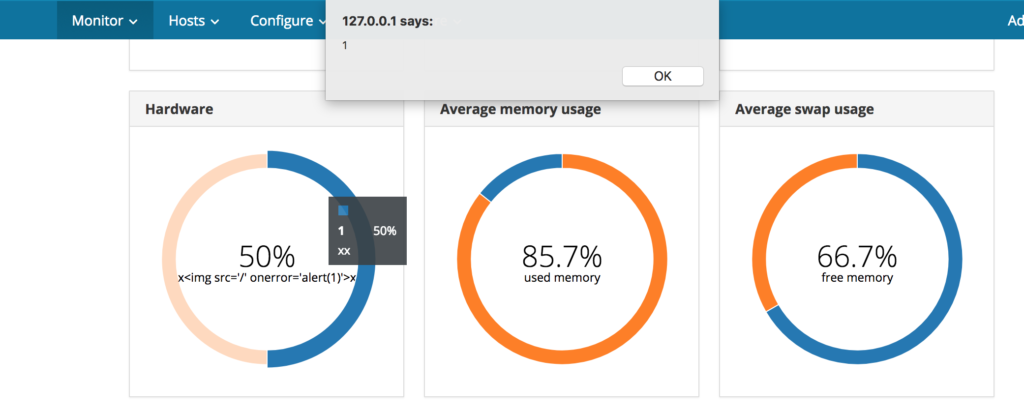
Still some interaction needed. I’ve noticed that on the general /statistics page the same graphs are used and facts like “manufacturer” are used in them. Unlike the other graphs these do not have a legend. But when you hover over a portion of the graph you’ll get a tooltip with the fact value. This is again vulnerable to XSS. For example add to xss.yaml:
manufacturer: x<img src='/' onerror='alert(1)'>x
Now when you visit the /statistics page and move the mouse over the hardware graph, the alert(1) will execute:
Still needs interaction. But if you inject a value into all the graphs it may not take long for an Administrator to hover over one of those.
However: By default Foreman uses CSP. Stealing someones session with this setup is not easily possible. So my initial plan to steal an Administrators Foreman session failed in the end.
This was tested on Foreman 1.15.6 and reported to the Foreman security team on 2017-10-31.
CVE-2017-15100 has been assigned to this issue.
A fix is already implemented and will be released with version 1.16.0.